Task Hijacking Vulnerability
Task hijacking is a vulnerability that affects Android applications based on how the Task Control features are configured in the AndroidManifest.xml file. This could allow an attacker or malicious app to takeover legitimate apps to steal information.
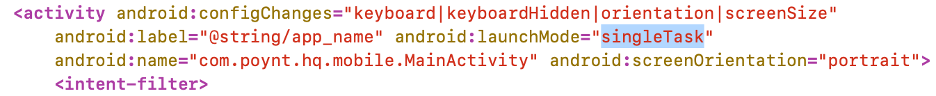
This vulnerability is based on the launch mode of the Activities the app creates. Check the AndroidManifest.xml file to review if the app is using a launch mode of ‘singleTask’ - which is susceptible and discouraged from typical use.
CVSS Scoring
Task Hijacking was assigned CVE-2021-33699 with a CVSS (Common Vulnerabilities Scoring System) Score of 5.7. To exploit this vulnerability, an attacker must be able to install a malicious application on to the victim user’s device. This requires the user to explicitly allow the installation of this app, as Android only allows installation from trusted sites, such as the Play Store, by default.
Proof Of Concept Exploit
If the app is susceptible to this vulnerability, create the proof-of-concept application to attempt the exploitation. You can download an example app at the link below. You will need Android Studio to compile the app.
Download the Android Studio project of the POC (Proof of Concept) app [here](https://secureservernet.sharepoint.com/:u:/r/teams/InfoSec_STARSOrg/Shared Documents/SRA Team/SRA/Mobile Penetration Testing/Custom-Exploit-Apps/Android-TaskHijacking.zip?csf=1&web=1&e=7khQ08)!
With the example app open in Android Studio, make the following changes to its AndroidManifest.xml file:
android:taskAffinity="com.example.appname"
This setting is the package name of the application task to hijack. Update this value to use the App ID of the application under test. Once the file is updated, deploy the app to your device.
-
Connect the test device to the computer running Android Studio
-
Click the “Run” button to compile the app and deploy to the device With the POC app on the device, the following steps will demonstrate the task take-over process:
- Launch the target app (the app you are testing)
- Check that it is shown in the “background” apps (optional)
- Go back to the main screen and launch the attacker POC app
- Check the background apps, and ensure the target app is there (the attacker app will not show up)
- Tap on the target app
- The attacker app should have taken over the target app task
- Check the background apps again, and it will show it as the target app heading, but it is really the attacker app
If this all worked, then the target application is vulnerable to the task hijacking vulnerability!
Mitigation
Evaluate the launch mode for the Activities in the app and change them to singleInstance if possible.
REFERENCES
https://blog.dixitaditya.com/android-task-hijacking?x-host=blog.dixitaditya.com