Network Hosts
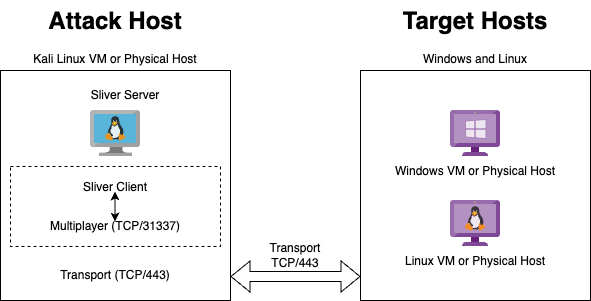
To fully use this workshop, you will need to have access to three hosts. They can be virtual machines or physical hosts if you have them. We will use one Linux host as the "Attacker" server, and then two other hosts (one Windows, and another Linux) to act as the "Target" servers.
In my case, the Attacker machine will be a standard Kali Linux host. For the Targets, I will use a Windows 11 VM and a Debian based Linux VM.