Biometrics Testing
Apple introduced biometrics in the iPhone 5S with the inclusion of Touch ID. Given the power that biometrics authentication would provide, Apple created a hardware-based key manager called the Secure Enclave Processor (SEP) to store this data.
Face ID was introduced with the iPhone X. Like Touch ID, this biometric data is stored in SEP. Based on the design of the iPhone X (and later models), Touch ID is not available. There is no fingerprint "button" to test against. So, the available biometrics heavily depends on the hardware model being tested with. If an iOS app provides authentication through biometrics, it must determine the hardware model in use and offer the appropriate biometric workflow (Face ID or Touch ID).
It is important to note that biometrics testing should always be performed on a physical device. While Xcode 9 can emulate Touch ID in the iOS Simulator, this should not be tested in that way - that is only available for Development purposes. Face ID cannot be emulated, so must be tested and developed on a physical device.
When biometrics are used for authentication, the user's credentials are stored in the device Keychain. This entry in the Keychain should be protected with access controls so that it is only available to biometrics. If the biometrics passes, the app pulls the credentials from the Keychain and passes that data to the app on behalf of the user. The Local Authentication Framework provides the necessary code for requesting data from the user with the provided security policies.
iPhone/iPad Sensors
The image below outlines the location of the biometric sensors in an Apple device capable of Face ID.

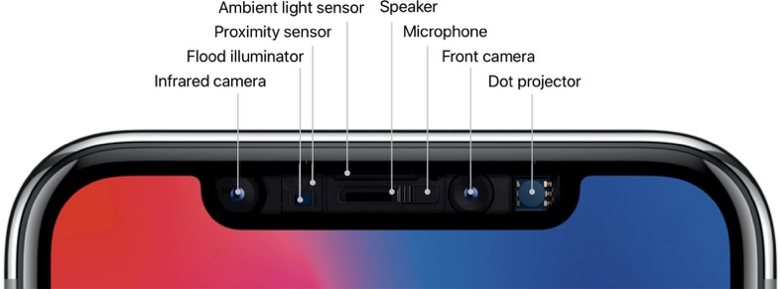
Touch ID
The image below outlines the the biometric sensor in an Apple device capable of Touch ID.


Test Case Outline
Presentation Attacks (Spoofing)
-
Presenting fake biometric data to the sensor in the mobile device.
-
Use still images of various resolutions to attempt to spoof the biometrics
-
Use a video for Face ID
-
Create fingerprints for Touch ID
-
-
Attacker enrolls in biometrics on the device.
Ensure the app requires the user to input the app credentials following any change to biometrics enrollment.
-
Enrolling a new fingerprint for TouchID
-
Resetting any TouchID enrollment
-
Enrolling in FaceID, or setting up an "Alternate View"
-
Resetting FaceID enrollments
-
Changes to the device passcode
-
Ensure the "attacker" is required to enter the device passcode before enrolling in biometrics.
-
-
Liveness testing
-
For FaceID, check that the "Attention" mode is set. Attention mode requires the user to look at the device for it to work.
i. Settings Face ID & Passcode Require Attention for Face ID (enabled)
ii. Settings Face ID & Passcode Attention Aware Features (enabled)
-
With Attention mode set, ensure that FaceID fails by not looking at the device during biometrics.
-
Test Face ID authentication with Attention mode enabled and disabled.
-
Brute Force Attacks
-
Test that the app keeps track of failed biometric attempts. Biometrics authentication should follow a similar guideline to passwords.
-
Test the app response to failed biometrics.
i. Does the app disable biometrics after a certain number of failed biometrics authentication?
ii. If the app does disable biometrics, does it require the user to enter the device passcode to re-enable biometrics?
iii. Does the app require the password after biometrics is re-enabled?
-
Dynamic Instrumentation Attacks
Performing dynamic instrumentation attacks will require the device to be jailbroken, or that the app has had an appropriate instrumentation framework injected into it. The examples below use the Frida dynamic instrumentation framework, but another alternative is to use Cycript.
-
Test the app to determine if you can bypass the biometrics authentication by providing false information to the sensor (i.e. use a fingerprint that is not enrolled).
-
Connect the device to the Mac with the USB cable, and launch the target app.
-
Determine the app name as Frida views it.
frida-ps -Ua -
Trace the running process to ensure that the app is using the "LAContext evaluatePolicy:localizedReason:reply" method.
frida-trace -U -m '-[LAContext evaluatePolicy:localizedReason:reply:]' 'App Name'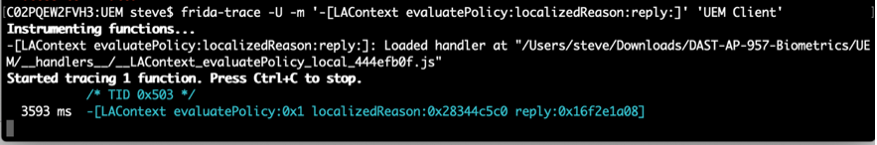
-
To determine its use, you may need to tap the home button (or swipe the app from the screen) and re-launch the app. The image above shows the app is using the method.
-
Test Case Details
For detailed test cases, please use the HTML document that is linked below. This can be used to document the results of biometrics testing.