Mobile Security Framework
Links:
https://github.com/MobSF/Mobile-Security-Framework-MobSF
https://mobsf.github.io/docs/#/
Starting MobSF
To run the application:
-
Change into the
Mobile-Security-Framework-MobSFdirectory -
To launch the app, execute the
run.shscript -
Open a web browser to http://localhost:8000
Analyzing the APK
To start the analysis of the APK, drag & drop the APK file to the web browser instance running MobSF. It may take several minutes for the analysis to complete.
Information
Once the analysis is complete, the app will take you to the "Information" section. This will provide basic information of the app, plus a security score and third-party tracker information.
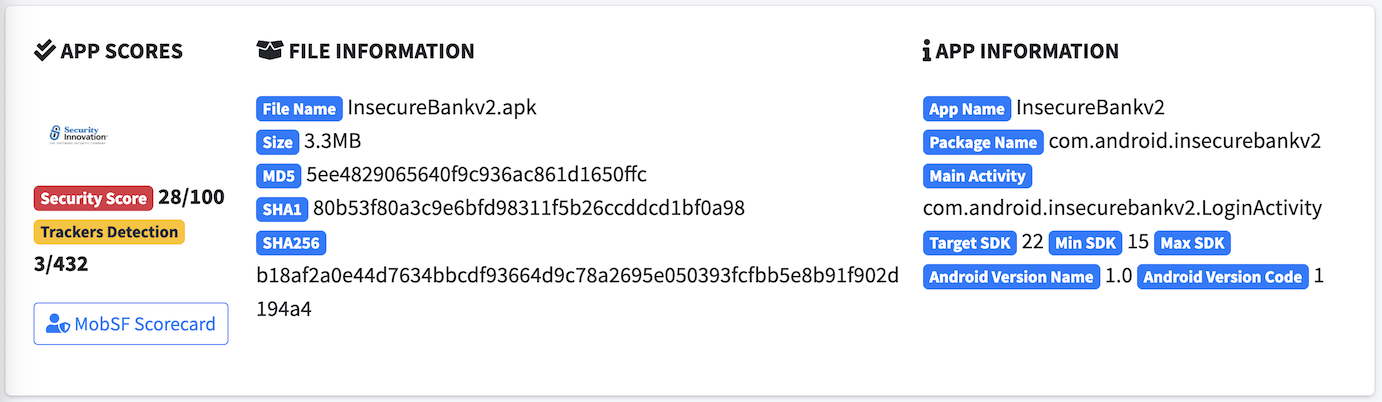
MobSF Scorecard
One item in the Information section is the MobSF Scorecard. This outlines the security score, risk rating, and privacy risk. It provides a quick view into the attack surface of the app.
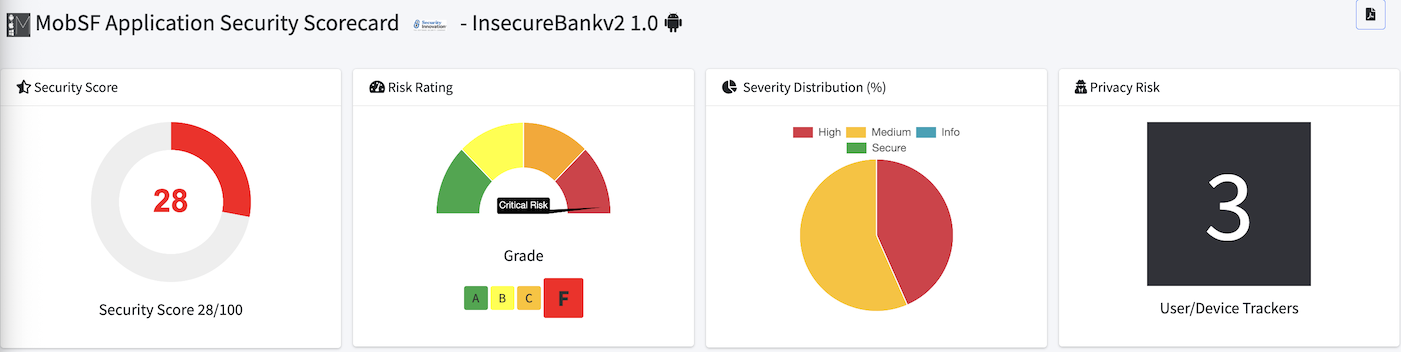
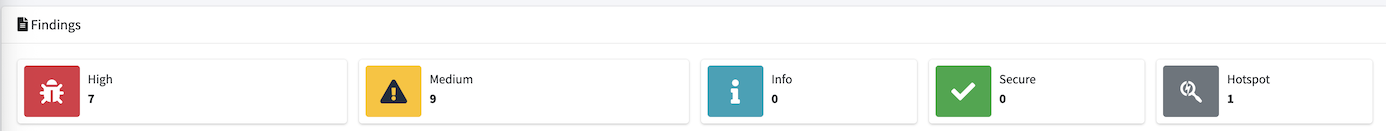
In the upper right corner, there is a PDF icon to save the Scorecard as a PDF.
Android Components
One thing to look for are the components of the app that are exported. MobSF makes this easy. Make a note of the exported components for ideas on how they can be exploited later on.
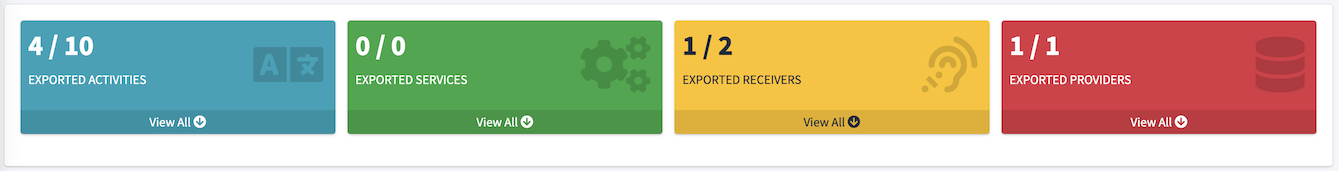
Security Analysis
MobSF has a security analysis section which outlines some of the app configurations and binary analysis. It also does a really good job at highlighting the potentially vulnerable configuration of the app. The following list is included in the typical MobSF output and all of this data should be reviewed!
- Signer Certificate
- Application Permissions
- Android API Levels
- Browsable Activities
- Network Security
- Certificate Analysis
- Manifest Analysis
- Code Analysis
- Shared Library Analysis
- Malware Lookup
- APKiD Analysis
- Abused Permissions
- URLs
- Trackers
- Possible Hardcoded Secrets
Note: Ensure to check for multiple pages for each of these sections so that you review all of the relevant information.